Moving data is part of everyday digital work, and SFTP is one of the safest ways to transfer sensitive information without exposing it in transit.
SFTP stands for Secure File Transfer Protocol. It runs over Secure Shell (SSH) to create an encrypted, authenticated channel for file transfers between a client and a remote server—even across untrusted, public networks.
Beyond simple uploads and downloads, SFTP makes it practical to manage large, sensitive files across networks. You can store, upload, rename, and access files while preserving data confidentiality and integrity.
Its core purpose is to reduce the risk to data sent over the internet and internal networks by enforcing encryption and strong authentication end to end.
What Is SFTP?
SFTP is an SSH-based file transfer protocol designed to provide a high level of security for moving and managing files. It uses a client–server model in which both sides are authenticated before any data is exchanged.
The Secure File Transfer Protocol originated in the IETF SECSH working group as an Internet-Draft and is widely implemented alongside SSH, but it never became a formal IETF RFC. In practice, most implementations (like OpenSSH) use SFTP protocol version 3. Understanding SSH helps you see how SFTP negotiates keys, authenticates parties, and protects every byte in transit.
In practice, a secure SFTP session comes together through four main components and steps:
- SFTP client software. An SFTP client initiates the connection and includes SSH functionality so it can authenticate to SSH servers using passwords, keys, or both.
- Server host. An SFTP server implements SSH and listens (by default) on port 22 for incoming requests. When a connection is attempted, the client and server identities are validated.
The initial TCP three-way handshake establishes the connection at the transport layer, after which SSH takes over to negotiate encryption and authentication across the internet and network layers. - Establishing connection. A session proceeds only after successful mutual authentication. SSH then establishes an encrypted channel, and file operations begin once encryption and key exchange complete.
- Firewall configuration. Firewalls must allow the SFTP service to communicate with clients—typically by permitting inbound connections on TCP port 22 (or a custom port if you’ve changed it) from approved sources.
Those are the essentials for a successful SFTP transfer. Several security practices are also built into the protocol and typical deployments.
Key elements of SFTP security include:
Authentication—When an SFTP client connects, it must prove its identity—usually via a password, SSH key pair, or both (often with multi-factor prompts). The server also proves its identity to the client using a persistent host key, preventing impersonation.
Authentication is not one-way. SFTP validates the user and verifies the server to the user, reducing the risk of credential theft and rogue endpoints.
Encryption—SFTP relies on SSH to encrypt the session. After an initial asymmetric key exchange, efficient symmetric ciphers protect the bulk data stream for speed and security.
Data integrity and confidentiality—Integrity is enforced with message authentication codes (MACs) or AEAD modes, ensuring packets aren’t altered in transit. Confidentiality is maintained by strong, modern ciphers throughout the session.
Robust file management—SFTP isn’t just a pipe. Clients can list directories, set permissions, resume transfers, and copy, edit, or delete files—all over the same secure channel. This is why developers and system administrators prefer SFTP for routine ops.
Improvements over FTP—Classic FTP sends credentials and data in plaintext and opens multiple ports, which complicates firewalling and exposes traffic to sniffing and tampering. FTPS (FTP over TLS) adds encryption but retains FTP’s multi-port behavior. SFTP is different: it’s an SSH subsystem that uses a single encrypted channel and modern cryptography, making it simpler to secure and audit.
Unlike legacy, text-oriented FTP commands, SFTP uses a packet-based binary protocol that’s purpose-built for secure automation and reliable transfers.
SFTP’s underlying technologies
SFTP is tightly coupled with Secure Shell (SSH), a cryptographic network protocol for secure remote access and tunneling over untrusted networks.
SSH encrypts credentials, identities, and data streams. In the SFTP context, SSH handles negotiation and key exchange, then maintains the secure channel while the SFTP subsystem performs file operations.
SSH and SFTP share the same goals—confidentiality, integrity, and authenticity—but operate at different layers. SSH works at the transport/session layer, while SFTP runs as an application-layer protocol over SSH.
SSH uses both asymmetric and symmetric cryptography: public-key algorithms establish trust and exchange keys; fast symmetric algorithms then encrypt bulk data. Common modern choices include AES-GCM and ChaCha20-Poly1305 for encryption and integrity in one step, or AES-CTR with HMAC-SHA-2 MACs. SFTP fully benefits from these choices.
SSH key pairs (e.g., Ed25519, ECDSA, or RSA 3072+) provide strong, phishing-resistant authentication without sending reusable passwords over the wire. Note: DSA keys are obsolete, and modern OpenSSH disables the legacy ssh-rsa (SHA-1) signature scheme by default—use RSA with SHA-2 signatures (rsa-sha2-256 / rsa-sha2-512) if you must use RSA.
Applications that use SSH typically follow a client–server architecture—which dovetails with SFTP. HTTPS (HTTP over TLS) is a secure alternative for web APIs and browser-based downloads, but for interactive file operations, automation, and server administration, SSH-based SFTP offers simpler firewalling and fine-grained access control.
How SFTP safeguards the file transfer operations
SFTP’s security comes from design choices as much as from encryption. A session starts only after the client and server successfully authenticate each other, and the entire exchange is confined to one encrypted connection.
Here are key protections SFTP applies:
Single, secure port—SFTP uses a single SSH connection (typically TCP 22). Fewer open ports reduce the attack surface and simplify firewall and IDS/IPS rules.
Tamper detection—MACs or AEAD modes ensure packets can’t be silently altered. Any mismatch is detected and the session is terminated.
Flexible authentication—Unlike FTP, SFTP supports strong identity proof: passwords (ideally with MFA), SSH keys, or both. SSH keys enable secure, script-friendly logins without interactive prompts.
These controls combine to make unauthorized access and in-transit manipulation far harder.
Username and password authentication—Simple to deploy and familiar to users. Strengthen it with strict password policies, rate limiting, and multi-factor authentication when supported.
SSH key authentication—Preferred for automation and admin access. Keys (commonly Ed25519) are far stronger than typical passwords and can be protected with passphrases and hardware tokens.
Regardless of method, the objective is to block unauthorized access. Keep private keys only on trusted clients and rotate or revoke keys promptly when access changes.
Server host authentication—The server proves its identity to the client using a persistent host key. Clients should verify the host fingerprint on first use (out of band) and alert on changes, mitigating man-in-the-middle attacks that try to proxy or alter traffic.
SFTP use cases and why it is a crucial technology
Security matters most when it solves real problems. SFTP is widely adopted because it protects everyday workflows without adding needless friction.
Common SFTP use cases include:
Safeguarding sensitive data—Businesses routinely share proprietary assets with partners, vendors, and contractors. SFTP’s encryption and authentication help prevent leaks of trade secrets and customer data during those exchanges.
Raising overall file security—Data in transit is a prime target for eavesdropping, credential theft, hijacking, and tampering. SFTP’s encrypted, authenticated channel sharply reduces exposure to sniffing tools and man-in-the-middle attacks.
Meeting compliance requirements—Regimes like GDPR, HIPAA, PCI DSS, SOX, and CCPA expect encrypted transport, access controls, and auditability. While they don’t mandate a specific tool, SFTP helps satisfy secure transfer, logging, and least-privilege requirements for regulated data flows.
Automating file operations—Enterprises run at massive scale: backups, nightly jobs, data feeds, and DR copies happen constantly. SFTP supports key-based, scriptable, resumable transfers so these tasks run reliably without manual intervention.
Using an SFTP Client
An SFTP client is the software that establishes the secure SSH connection to a server and lets you move and manage files over that encrypted tunnel.
Once connected, you can transfer files to and from remote machines, change permissions, synchronize folders, and resume interrupted transfers.
SFTP clients also expose file operations over TCP/IP networks you don’t fully trust. Typical capabilities include:
- Uploading and downloading files and entire directories
- Exploring and navigating local and remote file systems
- Managing content on platforms like WordPress via direct access to your hosting file system (with care and proper roles).
Most SFTP clients are native desktop applications for Windows, macOS, and Linux. Browser-based tools still exist, but Chrome Apps are fully deprecated on Windows and macOS, and web UIs often rely on gateways or limited permissions—so for security and reliability, native clients are generally preferred.
Before transferring files, create SSH keys and add them to your SSH agent, then copy the public key to the server account you’ll use.
With asymmetric cryptography, your private key stays on the client, and the server stores only your public key.
Step 1: Setting up the SSH keys
Git is a convenient way to practice SSH keys because it ships with OpenSSH on most systems and supports key-based authentication for remote repositories.
Start by generating a key pair on your local machine.
Launch the terminal
In this example I generate a key for a GitHub account using OpenSSH. Recent Windows, macOS, and Linux releases include the OpenSSH tools by default.
Generate a key pair with the Ed25519 algorithm
OpenSSH supports several key types. Ed25519 is fast and secure for most users (RSA 3072+ is a common fallback when needed).
ssh-keygen -t ed25519 -C “your_email@example.com”
This command creates a new SSH key pair and labels it with your email address.
After running the command, you’ll see output similar to the screen below, confirming key creation.
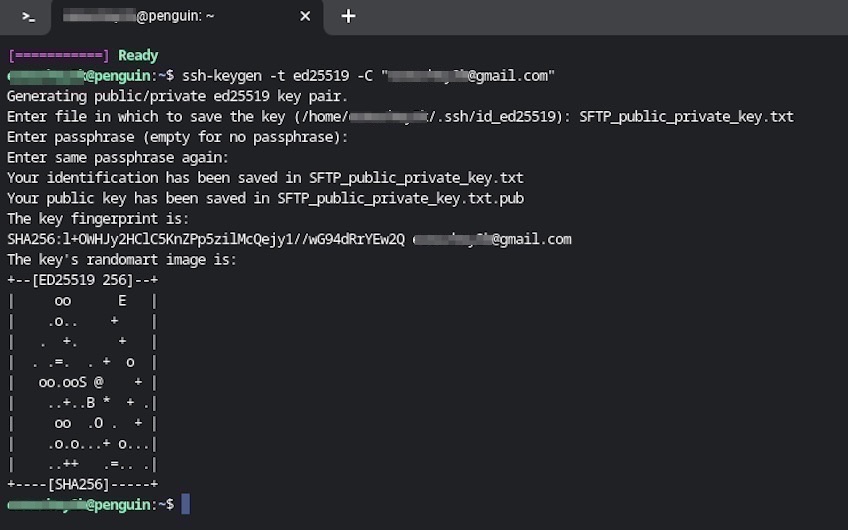
You’ll be prompted for a file location (accept the default unless you have a reason to change it) and an optional passphrase to protect the private key.
Step 2: Adding the new SSH Keys to the ssh-agent
Typing a passphrase every time can be tedious. The ssh-agent securely holds decrypted keys in memory so you can authenticate without re-entering it during your session.
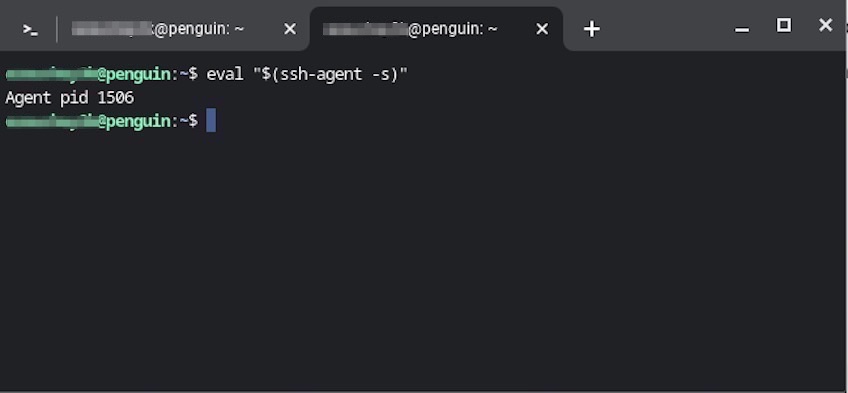
First, ensure the agent is running.
Run: eval “$(ssh-agent -s)” in your terminal, as shown below.
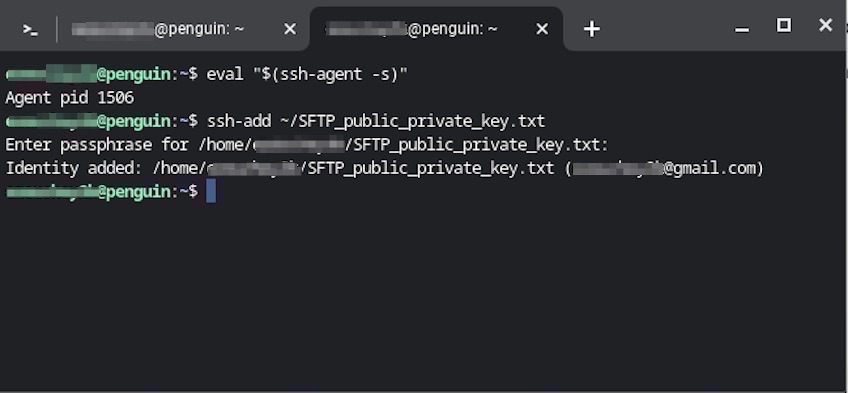
Then add your key with the ssh-add helper, pointing to the private key file (for example, ~/.ssh/id_ed25519).
Step 3: Copying the public key to the SSH server
The exact steps depend on your hosting platform or server OS. Many environments support ssh-copy-id, control panels, or web consoles to paste your public key (id_ed25519.pub) into the authorized keys for your user account.
Once configured, you can connect with your key and enjoy the reliability, speed, and safety benefits of SFTP clients for day-to-day operations.
Benefits of using an SFTP client
Fast, safe transfers—SFTP streamlines large data moves with resumable transfers, compression, and scripting—reducing time and human error while keeping everything encrypted.
Efficient server administration—Admins and developers can securely update configs, deploy releases, and manage logs without opening extra services or ports.
Seamless integration—Quality SFTP tools integrate with firewalls, VPNs, secrets managers, and schedulers, improving throughput, security, and team productivity.
Popular SFTP Clients
SFTP clients give you direct, secure access to files on websites and remote servers. They improve productivity for development, web design, data ingestion, and content management workflows.
The best clients typically let you:
- Upload, download, rename, delete, and set permissions on files and folders
- Verify integrity and resume interrupted sessions
- Enforce encryption and authentication with modern SSH protocol support
- Log activity for auditing, compliance, and troubleshooting
- Handle bulk uploads to CMS roots (e.g., WordPress) with appropriate user roles and backups
Many clients are free or offer generous free tiers alongside paid upgrades for advanced features.
An overview of the most popular SFTP clients
- SolarWinds Solar-PuTTY—A free Windows terminal utility that supports SSH, SFTP, SCP, FTP, and Telnet in one tool.
- WinSCP—A Windows-only FTP/SFTP/SCP client with a friendly GUI and powerful automation via command-line and .NET assembly. Also supports WebDAV and Amazon S3.
- Cyberduck—A clean, open-source SFTP/FTP client for both Windows and macOS. Integrates with storage platforms like OpenStack Swift, Backblaze B2, Microsoft Azure & OneDrive, Google Drive, WebDAV, Amazon S3, and Dropbox.
Extra functionalities with paid software
Paid tiers typically add features that boost scale, security, and usability for larger teams and regulated environments.
Common premium capabilities include:
- Advanced security—Geo-based access controls, custom certificates, on-prem agents for behind-the-firewall transfers, IP allowlists, and granular role-based permissions.
- Compliance & auditing—Centralized logs, tamper-evident archives, retention policies, and flexible governance to align with industry regulations.
- Integrations—Connectors and iPaaS options that trigger workflows across hundreds of third-party apps and cloud services.
- Global support—Internationalization, multilingual interfaces, and region-aware storage options.
The top three SFTP clients
SolarWinds Solar-PuTTY
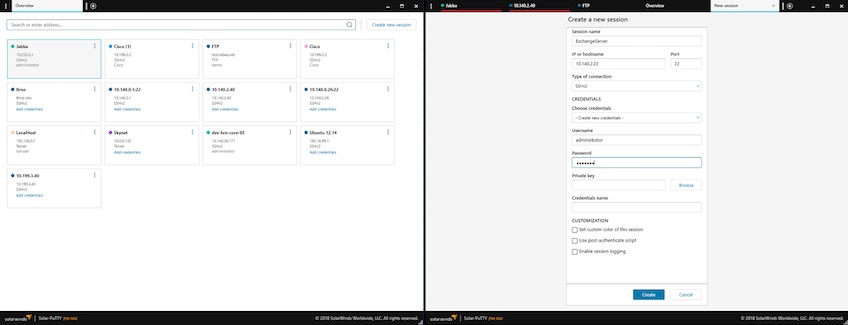
Solar-PuTTY is a free, standalone Windows terminal built on the popular PuTTY client. It centralizes SSH, SFTP, SCP, FTP, and Telnet so you can manage sessions from a single interface.
SolarWinds Solar-PuTTY standout features
- Session & credential management—Save usernames, passwords, and private keys per session for quick, authenticated logins.
- Tabbed, multi-session workflows—Run and organize multiple active connections in one window.
- Post-connection scripting—Automate routine commands the moment a session connects.
- Windows integration—Find saved sessions via Windows Search and pair with SolarWinds tools (like ipMonitor) for deeper visibility.
Pros
- No installer required—just run it.
- Professional remote session management for teams.
- Browser-like tabbed interface for ease of use.
- Recalls existing PuTTY sessions.
- Keeps PuTTY’s strengths while adding modern conveniences.
- Broad protocol support for connecting to almost any server.
Cons
- Interface and options are tailored to network and DevOps pros, which may overwhelm casual users.
WinSCP
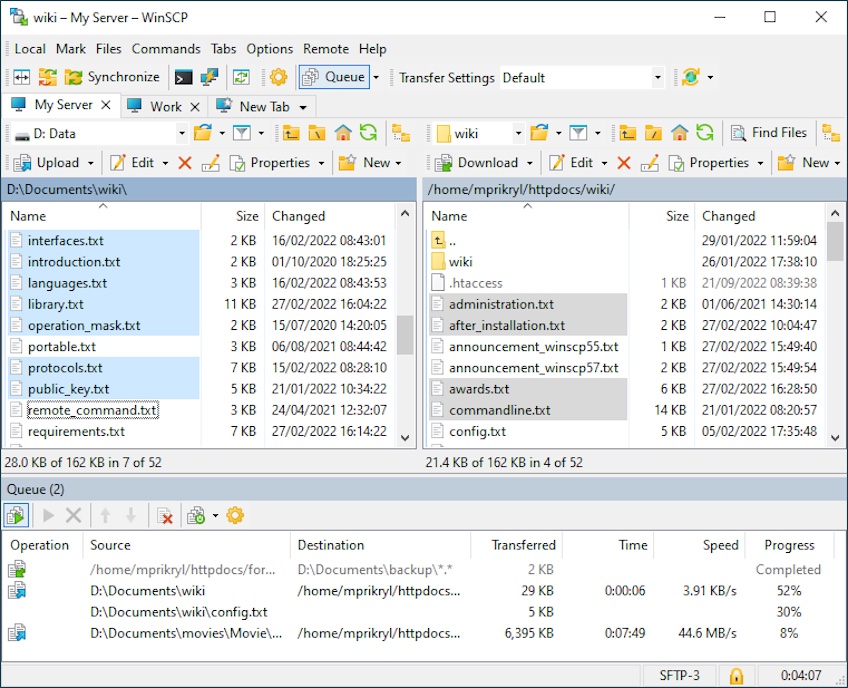
WinSCP is a Windows favorite for secure file transfers. It supports SFTP, SCP, FTP, and WebDAV, and includes a lightweight file manager with synchronization and remote editing.
WinSCP standout features
- Robust CLI & scripting—Automate repeatable jobs with command-line scripts or the .NET assembly.
- App integrations—Integrates with PuTTY and Windows apps for streamlined workflows.
- Task automation—Powerful scripting for syncs, backups, and batch transfers.
- Advanced transfer options—Directory caching, binary/text modes, and the ability to open shell sessions for remote commands.
Pros
- Small footprint with minimal resource use.
- Open-source and free.
- Offers both GUI and command-line interfaces.
- Large community and extensive documentation.
Cons
- No full terminal emulator.
- Windows-only.
- Basic built-in text editing.
- Transfers of very large files may need tuning for best performance.
- UI feels dated compared to newer tools.
Cyberduck
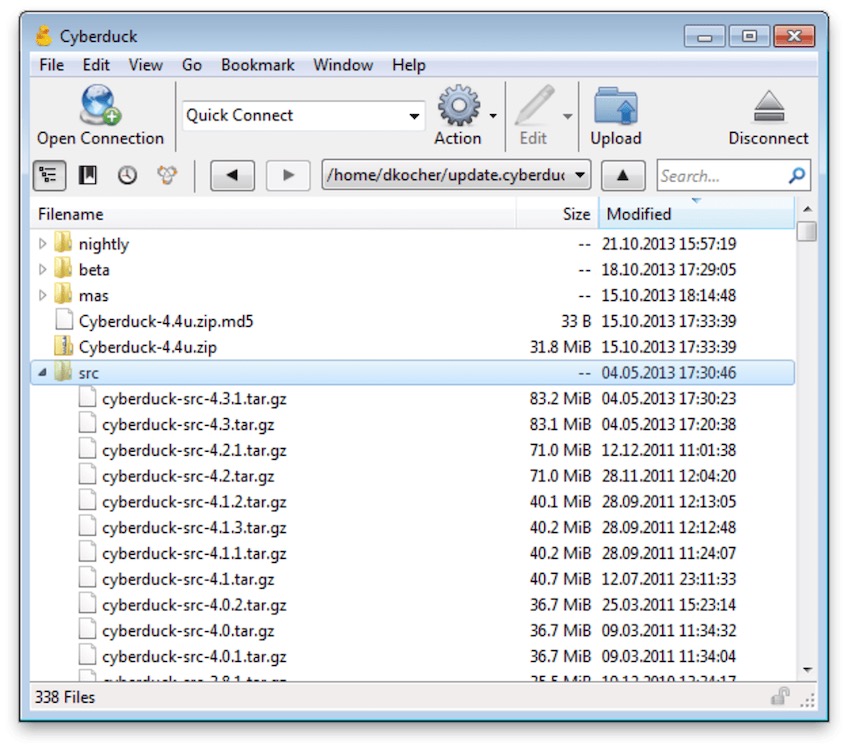
Cyberduck is a free, open-source SFTP/FTP browser known for its clean UI. Originally for macOS and now on Windows, it connects to popular cloud storage providers and traditional servers alike.
Cyberduck standout features
- Easy file management—Intuitive drag-and-drop plus copy/paste for moving data quickly.
- Wide integrations—Connect to Dropbox, Oracle Storage Cloud, Google Drive, OneDrive, Microsoft Azure, OpenStack Swift, Amazon S3, Backblaze B2, WebDAV, and more.
- Editor preferences—Open files directly in your preferred external editor, then save back to the server.
- Keyboard-interactive SSH—Supports one-time passwords and interactive prompts.
- Client-side encryption—Create Cryptomator-based vaults so data is encrypted before it leaves your machine and remains encrypted at rest on remote storage.
Pros
- Minimal, user-friendly interface.
- Runs on both macOS and Windows.
- Optional encrypted credential storage and client-side vaults.
Cons
- No native Linux desktop build.
- Extra security features (like on-the-fly encryption) can impact performance.
- Drag-and-drop reliability varies by platform and file manager.
Conclusion
Of the three, SolarWinds Solar-PuTTY is a strong all-around pick on Windows. It’s free, supports multiple protocols, and adds modern session management over classic PuTTY. If you prefer a dedicated file-centric UI, WinSCP and Cyberduck are excellent, mature alternatives.
